Protecting your business by securing endpoint devices
Datto
Datto work with local specialists, primarily around Backup. They were founded in 2007 and have 22 offices around the world. 520+ petabytes of data are protected by Datto - that's 1,000 x more data than Spotify's entire music library. They have data centres all around the globe, partnering up with local experts.
What Servers and Business Critical Systems Do We Need To Protect?
Is your server local or cloud hosted?
Examples of business critical cloud hosted applications include:
- Exchange email server - Office 365, Gmail
- Files, folders and company data - Sharepoint, OneDrive, Google Drive, file sharing tools
- Accounting and invoicing systems - Quickbooks Online, Xero, Freshbooks
- Company website - Azure, Amazon Web Services, Squarespace
- Domain Controller (user accounts, passwords, (etc) - Azure AD
If your applications are not on one of these services, chances are they are running on a physical server, either in your office or at a different location, which leaves you potentially vulnerable in the case of an outage.
Local Servers
Business Tools
- Printer connections for the office
- Internet traffic and network controls like VPN, DHCP and DNS
- Local login management (AD)
Data Not Suited To Cloud Working
- Design projects, photos and videos that are too large to always synchronise over the internet
- Highly confidential data, or restrictions by industry
Local - Only Systems
- Production and application software that can't run in the cloud
- CCTV and Security (such as door entry systems)
- Some desktops like booking systems, factory terminals, and editing/design rigs
How To Protect Physical Servers
Backup vs Business Continuity
Business Continuity is the extension of backups. Not only do you want to be able to get your data back, you need to be able to do it in a very short space of time.
The Causes of Downtime
24 %: Human error. EG, pulling out a plug to plug in something else
26%: General outages due to loss of internet to the building. EG, external building works which cut through a cable
11%: Natural disasters: EG, floods, fires
23%: Ransomware & Malware: the one to watch, as this is rapidly increasing, and targeting businesses specifically.
What is Ransomware?
Ransomware is a small programme that gets run on your computer.
Sometimes attackers already have access to your systems, and when the time is right they will launch their attack.
Sometimes it's a trojan horse attack, where a file appears to be something that it's not, often a pdf or excel document.
Later in the webinar we'll see a live demo of a ransomware attack. The reason that ransomware is so vicious in in many ways is that it can attack a entire system extremely quickly.
If you were to mount an attack to download someone's data from their computer, that would take a lot of time - maybe a day, maybe multiple days to download the data. You might choose to do it very slowly, so that it goes under the radar. As soon as it's got access the ransomware attack can hit and encrypt anything it sees. As much as we love fast powerful computers it works against us in this case, as the processor speed means that we can go through an entire file system and essentially lock those files or encrypt them.
The attackers ask you to pay in Bitcoin, an untraceable currency - or at least very hard to trace - to get your money back.
How To Help Prevent Ransomware
No one's going to be 100% safe - even the biggest businesses - because the attacks are always mutating and finding new ingenious ways to attack people.
1. User training
This is key, as we'll see that in the demonstration of the actual attack later in the webinar. Ransomware is not really going after the central business's servers directly, it's looking for any entry point it can and it will use whatever mechanism.
Most often it is end users being overly trusting, and not thinking twice before running a file that they didn't realise was malicious. It is the old story - you can put the fanciest security systems on your front door; you can have iron bars; you can have expensive locks - but if you've left the side window open on your house then that's the obvious way for someone to get in.
We're looking to kind of review the entire environment and make sure there is no easy entry mechanisms and just some basic user training goes a really long way to encourage people to mitigate the risk of an attack.
A lot of people fear that if they told their IT admins or they told their bosses that they had accidentally ran a cyberattack on their own network, then they'd get in a lot of trouble - and that's the opposite response of what we want we want. We want people to own up as soon as possible; and although not rewarded, but praised for coming forward and admitting their mistakes because that gives us the best chance of recovering data and minimising the attack. Try not to punish people who mess up.
One example of humans being humans is this chap who was working in Hawaii, in the US. He got in the news in I think it's January 2018 for accidentally pressing the red button that warned every residence in the entirety of Hawaii that a nuclear missile was heading for their Islands and they should take immediate cover now. It was an awful example of a simple user mistake, which went global, and to make matters worse, he had stuck his passwords on to his desktop screen. This is a very nice example of giving people the right tools - if he had an easier way to remember his password, such as a password manager, he wouldn't have needed to write it out. Keeping your employees trained is everyone's responsibility, not just those who are the highest up, or the people with most access to technology. Everyone needs to be aware of the basics of cybersecurity.
2. Good Security Tools
These include:
- Antivirus
- Spam filters
- Firewalls
These technologies have been around for a while, they're always evolving and these businesses do a fantastic job to stay up-to-date.
3. Make Ransom Value Useless
You've probably got all of the above in place. One of the ways to prevent ransomware is to look at what the ransom message is all about.
They're trying to tell us that they have exclusive access to our data and they're asking us to pay money to get that data back - essentially telling us how much is that data worth.
I have a backup from five minutes ago and I can get back up and running in a matter of minutes, because I have a continuity set up rather than just backup. That ransom means nothing and I'm essentially going to ignore it.
You shouldn't rely on any one mechanism to prevent prevents attacks, but actually recovering from an attack is pretty straightforward.
You need to make sure you've got copies of your data in multiple places and you need to make sure that you can get that data back, fit for purpose, so you can be running your business again in a short period of time.
There have been a wide range of different cyber attacks based around ransomware, some of them hit Mac computers, some of them hit Windows. They have all been prolific and there are variations of every single one, because as soon as there's a fix for one of these particular attacks, the business that made the attack will just create a slight variation. There are still plenty of one person hackers sitting in a room somewhere, but increasingly there are actual businesses based around the world that will build an attack to order. You can go on the dark web, request an attack designed for a certain business, and it will be built for you for a fee.
What is at Stake?
We talked a lot about ransomware; we've talked about some of the mechanisms to prevent it. Why are we putting so much value in this recovery time? Downtime is costly. The average cost for small and medium businesses in the UK is £7,000 per hour.
There are two ways of estimating costs. Short term you're going to be paying wages, but for no activity; customer orders can't get processed; new business is lost and unfortunately if someone can't order with you they will probably go to a competitor.
In the weeks and months and years afterwards, reputation is going to play a massive part: everyone reviews everyone online these days and if your business has been unfortunate enough to have been the subject of a news article about a certain attack, that looks very bad to potential customers.
The cost of recovery can be huge, even if you have insurance. If you're in a regulated industry and you have committed to protecting data, losing that data might mean fines and penalties.
The Role of Datto
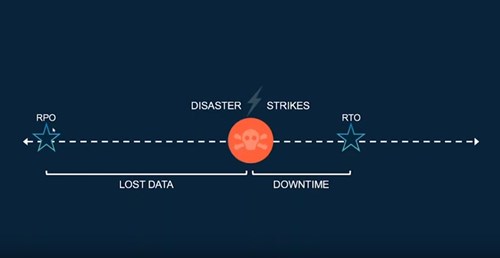
Recovery Point Objective
How far back in time is our last Recoverable Point? This is the amount of lost data we might experience. If you're doing a daily backup, then your Recovery Point is going to be 24 hours and anything done in the last day is essentially lost.
We want to make this as short as possible and potentially lose only an hour's worth of data or even down to five minutes with Datto.
Recovery Time Objective
This the second objective to consider. Let's say this disaster has occurred. How many minutes, seconds, hours, days does it take us to get fully back up and running? Given the hourly cost of an outage, there's no doubt that everyone would like this to be zero seconds or minutes. You'd want this happen immediately - but it's still going to take some time to get back up and running. We want to minimize this and make sure that our business is ready to take the hit of the amount of money it's going to take us to recover - that's the downtime calculation.
What Does Datto Do
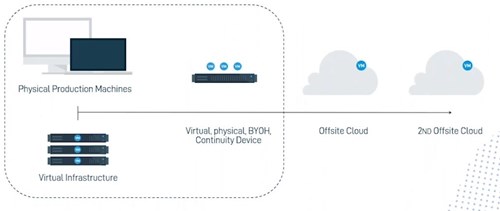
In the diagram, you'll see how Datto follows the "Rule of Three" (and potentially the rule of four), the backup mindset that says you should have three copies of your data.
The original, (on the left, running on the server);
A second copy, sitting on a box, inside the network - the dotted line shows this is inside the office
We've then got a Datto box installed which has got plenty of storage space for all of the different backups we're taking, maybe three month's worth of backups are available, directly from the local Datto box.
The Datto box will then replicate the data back to our private cloud. (We'll be very happy to go through the legalities, security and compliance of our cloud; it's a private cloud; for UK clients, this will be based in Slough, for European clients, we've got datacenters in Iceland and also in Frankfurt, Germany. If you'd like to, you could use one of those second clouds as a replication.
So you could have your first backups sent to Slough and then replicated to Iceland if you'd like to as well.
It is a very automated setup, which is important. You don't want to rely on old mechanisms. People used to back up to tape and people would be sent on a daily basis, to go downstairs and take out one set of tapes, lock them in the cupboard somewhere and put in another set. It is a painful setup because if someone's ill and it doesn't get done, then you've lost some of your backups. It's also a huge overhead; the actual hours that you're paying someone's wages just to go running around with tape.
Datto provides every step in this process, and design the entire strategy for how this works; Datto software backing up to Datto hardware, pointing at Datto cloud, and then providing continuity.
The blue circles on the diagram, saying "VM" stands for "Virtual Machine". The way that we work is that whatever backups you've been taking from your original devices, when they're sitting on the Datto device, we can actually turn those on as virtual machine computers on the Datto box.
For example, you had a massive outage which knocked out your email server; or a hardware failure (another common outage mechanism). If one of your computers is knocked out, the Datto device can turn on, as if it was that particular failed server, running it as a virtual machine, and that could be at backup point that was taken only five minutes ago. It can be turned on to take over where the original server left off. If another server went down, we could use this Datto device to run multiple servers.
If there should be an entire outage of the office, we would not be able to access the Datto device, however our cloud (also marked in the diagram with VM) can also run these virtual machines. This is little bit more involved, we'd recommend you do a dry run with Chess to practice how that would work in your environment. It could be that you have a second office location that you're able to go and work from, it could be that your employees go and work from home, connecting from their laptops to Datto's cloud. From there they access the servers just like they normally would, processing invoices, creating and sending emails etc.
Ransomware Attack
This remote machine is going to be our victim for today. It's set up ready to go. I have got my Datto device, which is protecting this server along with many others. (The Datto device tests your backups on a daily basis, for every server and will show you a successful screenshots of the the backup working and ready to use.
We're going to make a new document called Chess ICT Data, containing the time and date, and real time text information, to demonstrate that this is up to data information. In a real environment we would probably set this up to be an every five minute backup, and that's how much data we could lose.
Normally an attacker wouldn't go directly to the server, so this is slightly unrealistic in one sense. What would normally happen is that a user, looking for something they needed, downloads a file, eg an installer for a program that they have to set up.
It could be an email, eg as in this example, with a document called "Payroll and Bonuses", that looks like it was sent from the correct email address - it's quite easy to pretend to be someone else in an email, so the email address is correct.
The user double-clicks, and opens not a document but rather a type of application, which runs around the machine, taking any user data, including, in this instance, the test document, Chess ICT Data.
Every single file is now encrypted, and shortly afterwards there's a pop-up, saying that files are encrypted and to send Bitcoin to an address. One Bitcoin is now worth thousands of pounds. A ransom could be a fraction of a Bitcoin, approximately £300 - £1,000. How much is asked for varies - sometimes hackers they don't actually know which businesses they've hit.
Trying to convert the document back doesn't work; in this example, the time stamp is gone, as is the text. This is proper encryption; the server is now locked down. To give you a flavour of how this would happen in a more realistic environment, the attack will have been run from a desktop or a laptop, and as soon as it started running, it would look around the network and try and hit as many files and folders as it could, including your F Drive and any other computers that you can access.
Recovery
If you wanted something simple, eg if this was restoring just a couple of documents there's lots of flexibility to go in to a particular server, do a file restore and navigate around to recover files and folders. This is probably the most common restore done with any kind of backup system, whether it's continuity or not. It's useful to know that you can just get files and folders back when you need to.
What makes Datto special is that we can do a local virtualization. The local Datto box, sitting in your office, able to turn on, just as in the example of the server that had just had an outage.
The most recent backup point, that's been hit with ransomware is going to alert Chess that there is ransomware in the network, it's a very good early warning system, and they can investigate as soon as possible.
They will want to restore back to the backup that happened just before the ransomware attack; start the restore from here and they will choose suitable settings in here, maybe put it back into your network so it behaves exactly like the old one.
They're going to click start - this process is exceptionally quick. Some servers will turn on in a couple of minutes, some will turn on in a matter of seconds. The server, is still completely out of action, but we've got back up and running on the Datto box.
I've got My Documents folder with the Chess ICT data back in exactly how it was. What you've just seen there is a ransomware attack, hitting my chosen machine and we've actually been able to recover data that was written to it very shortly before that ransomware attack hit, which is exactly where you want to be.
At this point in time, whatever the server was doing; emails, files, finance system; that carries on running.
We can now turn off that the computer that got hit. Chess can go and investigate, maybe repair it; rebuild it; recover it; so that you can go back to your original systems at a future point in time.
You can take that steadily, schedule it for out of hours for any server work that needs to happen and the business carries on running happily from this this failover device.
Office 365
The first obvious thought for a lot of people is:
"Microsoft and Google backup the data already don't they?"
The answer is
"Yes, they do have some version control built in, so if you delete something it doesn't completely get wiped, it goes into your recycle bin.
It might sit there for a month or so before it gets removed from your recycle bin. If you delete it from the recycle bin, the admin does have an access to go in and look for old data; 30 days for Microsoft; 24 days for Google"
it's quite a pain to do, and it's on a file by file, folder by folder basis. You can't go in and get someone's data back to how it was yesterday, for example.
Microsoft and Google don't guarantee that your data is backed up. They guarantee that they will provide certain availability, so you'll be able to access your systems at all times; but data loss is not really going to happen from Microsoft wiping your data by mistake.
People lose data because humans are humans. They delete things, they overwrite the same filenames, and if you look in the actual service agreement from Microsoft (Google Services Agreement Microsoft) there are two sections where it says to regularly backup your content and data.
The first one is in reference to an outage:

The second reference is in regard to cancellation of services. Data will be deleted, so you should have a regular backup plan.
If you stop services with Microsoft, your backup plan probably has to come from someone else.
For Office and G-Suite, we do a cloud to cloud backup, which means essentially you don't have to have a big box running in your office to take all these backups; we have our datacenter in Slough and we replicate from the Office 365 datacenter, to our datacenter.
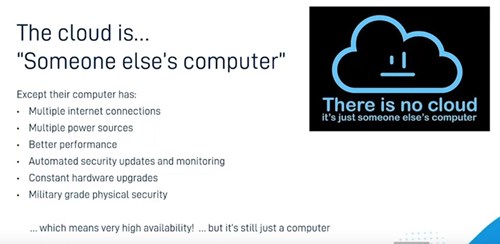
The cloud offers great products with fantastic security and very high availability, but it's still ultimately a computer and people interact with it in similar ways. People delete data, or once in a while there will be a outage from hardware failure.
Losing Cloud Data Is A Very Common Risk
One in three businesses have lost data from a cloud-based application; a third of all businesses have lost cloud data of some significance
Of different cloud-based ransomware attacks, 49% affected Office 365, and this is on the increase, because of course Office 365 is the most commonly used cloud service.
The time lost in attempting a recovery can be very damaging.
Datto focus on the ability to do backups from from Office and G-Suite, to get up and running quickly and to do fast recoveries.
It's a Very Human Risk
Data in cloud-based applications is vulnerable to:
End-user deletion, whether accidental or malicious
Malware damage or ransomware attacks
Operational errors such as accidental data overwrites
Lost data due to cancelled user licenses
Misconfigured application workflows
Office 365 and G-Suite offer data availability, they don't make claims on being able to backup data. Instead they suggest you use different products to do backups.
Data Protect for M365
Office 365
3 x daily automated backups for:
- Contacts
- Calendars
- OneDrive
- SharePoint Online (including Teams Sites)
G Suite
3 x daily automated backups for:
- Gmail
- Contacts
- Calendars
- Drive
- Team Drives
Datto can also trigger an extra backup if needed, for example if someone is leaving the company and you want to capture everything from their emails and from their Onedrive.
This goes direct to the Datto Secure cloud, where the physical service is being backed up - and does a potential infinite cloud retention, which means we can keep the backups in our clouds for the entire duration that you're using our product. (There are fewer versions, the further you do back, eg monthly versions if you go back five years.)
For compliance reasons, finance and legal industries may have legal requirements to keep up to seven years of backups. Datto do point in time snapshots and we can restore an entire account.
This has to go hand-in-hand with security compliance. Datto employ 256 bit encryption which means it's extremely difficult to get into the data in transit. We've got different compliances for various sectors, please get in touch for more information.
Speak to a Specialist
You can fill out the form and one of our product specialists will contact you shortly with more information.



About the author
Chess
Chess is one of the UK’s leading independent and trusted technology service providers, employing 300 skilled people across the UK, supporting over 20,000 organisations.
By leveraging world-class technology, Chess helps you to connect your people, protect your data, grow your business, reduce your costs and work better together, which means your business, your people and your customers can thrive.
At Chess, we’re passionate about our unique culture and our continuous investment in our people to be industry experts. We’re extremely proud that our people voted us No.1 in ‘The Sunday Times 100 Best Companies to Work for’ list 2018, and we continue to celebrate more than ten years in the top 100.