SASE – Secure Access Service Edge | Cyber Security Solutions
Protect.
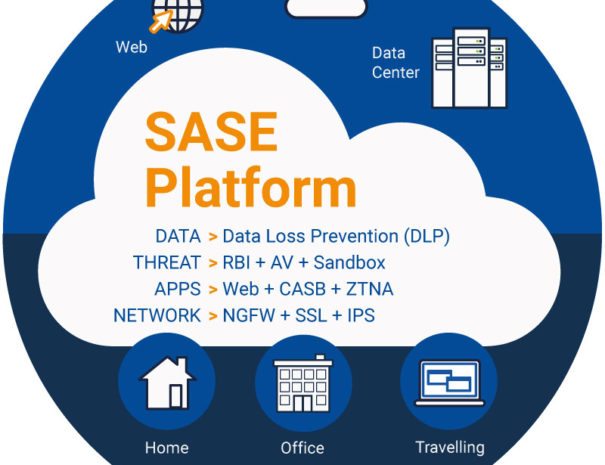
Secure Access Service Edge
SASE is a new approach to networking and security, protecting access to web, cloud, and private applications. Providing access to your people anywhere, anytime, and from any device.
Combining VPN and SD-WAN capabilities with cloud-native security functions, such as Secure Web Gateways, Cloud Access Security Brokers (CASB), Firewalls, and Zero-trust Network Access, SASE delivers a unified cloud-native service.

Protecting Your Organisation
The SASE framework integrates advanced security services, real-time threat detection, identity-based access controls, and secure connectivity within a cloud-native architecture to protect your users and systems against a range of online threats.
Malware & Ransomware
Malware can replicate and spread from devices to your internal servers via shared resources and lay in wait for days or weeks before it strikes.
Phishing Attacks
Without the email and web tools to identify and block suspicious emails and malicious links, your people are open to phishing attacks.
Data Leakage & Loss
If you do not understand your data landscape and enforce a data leakage prevention policy, your sensitive data could end up in the wrong hands.
Insider Threats
Your own people may be one of your biggest vulnerabilities, with staff misusing their privileges to gain unauthorised access to sensitive data.
Unauthorised Network Access
Malicious actors will try to access areas of your network you would rather stay private, gaining access to your systems, applications, and sensitive data.
Man-in-the-Middle Attacks
Unencrypted communication between users and apps can be intercepted, allowing attackers to eavesdrop or alter your data.
IoT Compromise
Unsecured Internet of Things devices are vulnerable to remote access and control by attackers.
Web Application Attacks
SQL injections, cross-site scripting (XSS), and other web-based threats can be used to target your people online.
5 Simple Steps to SASE
SASE solutions must enable people to work safely and efficiently, without inhibiting productivity. Empower your team to get the job done, wherever in the world they are at the time.
Keep control of your sensitive data by granting users access to only the resources they have explicit permission to use, under the oversight and control of your business.
SASE must provide continuous oversight of how vital data and intellectual property is utilised after being downloaded from apps, safeguarding against the transfer of data – either unintentional or malicious.
Remote users must have fast, secure, and reliable access to web, cloud, and private apps without the costs or complexities of private MPLS lines or backhauling traffic to HQ. Easy integration with SASE services is crucial for management at scale.
Controlling data usage, especially on remote devices and cloud services, requires an ongoing understanding user behaviour, and how it creates risks that could become breaches.
Secure Everything, Everywhere With CyberLab
With the ongoing shift to hybrid work, it is likely that you have already implemented some of the SASE components. Our team of experts can help you to build a structured plan to adopt the SASE framework.
Fortify your defences with a converged suite of security functions to ensure your people can work securely, efficiently, and flexibly.
Detect.
The first step to cyber security is to gain a complete understanding of your defences, and how well they are performing.
Our online Posture Assessment tool is a simple way to gain a better idea of your cyber security posture. Based on the NCSC 10 Steps to Cyber Security, it only takes half an hour to complete and it will help you prioritise aspects of your security.
To gain a better idea of your current posture, our CHECK and CREST certified engineers may recommend you begin your SASE journey with External Penetration Testing, Cloud Infrastructure Penetration Testing, or a Cloud Security Configuration review.
Protect.
Our team of cyber security professionals will guide you along your SASE journey.
We will optimise your team's productivity with seamless connectivity to apps in any environment and use a multifunction cloud security service to deliver enhanced protection and eliminate blind spots.
We will also improve scalability with cloud resource provisioning, and streamline your networking and security functions to eliminate the need for stand-alone firewalls, VPNs, and WAN optimisation devices.
Support.
We will equip your team with the knowledge and guidance necessary to utilise your new systems or programs effectively. Once your solution is in place, you can request support direct from the vendor, according to your service level agreement (SLA).
Additionally, you can take advantage of our years of experience supporting and maintaining the solutions with our range of Security Support services.
We'll look after the maintenance and configuration elements to ensure they are always in-line with industry best-practice, giving you both peace of mind and the time to focus on your other priorities.
Book Your Free 30-Minute Consultation
Our expert consultants are here to take the stress away from cyber security.
Whether you have a pressing question or big plans that need another pair of eyes, discuss it in a free 30-minute session an expert consultant.
Speak With an Expert
Enter your details and one of our specialists will be in touch.
Whether you’re looking to implement basic cyber security best practice, improve your existing defences, or introduce a new system or solution, our team of expert consultants, engineers, and ethical hackers are here to help.
Our team specialise in creating bespoke security solutions and testing packages to improve and maintain your security posture.
We are 100% vendor agnostic and will only ever recommend the best products and solutions for your requirements.